Page summary
Custom reports set s3 bucket permission
Setting the S3 Bucket Permission
- In AWS, create a user for the bucket. Make sure that this user has programmatic access:
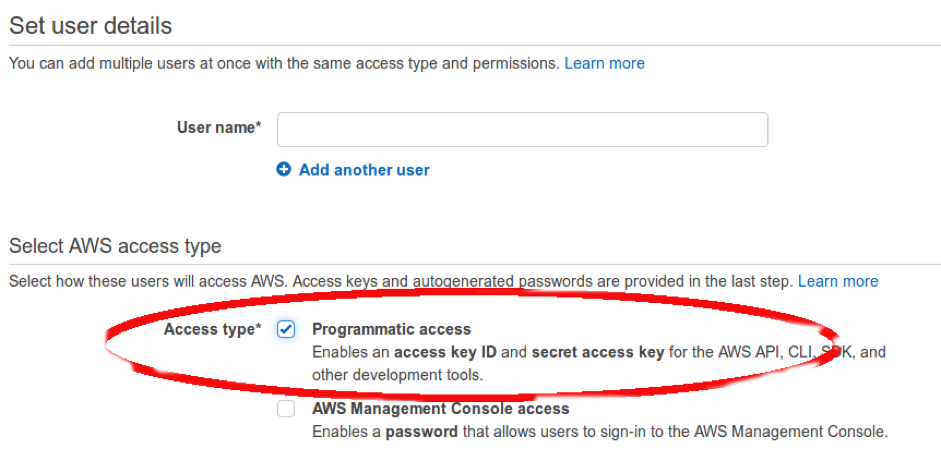
- For now, leave the permissions empty and click "Create user". Note to yourself the Secret access key as you won’t be able to see it again (You can also download it). In case you missed it, you may need to delete this access key (not the whole user, just the key!) and create another one. You can create up to two keys.
- Create a bucket. This name has to be unique across S3. DNS name is recommended (e.g com.mydomain.betterezbucket). You can select many advance option, but for this tutorial, leave all as is (use default).
- Go back to the IAM console, click Policies and Create policy.
- Go to the json section and paste the following code:
{
"Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "s3:ListBucket" ], "Resource": [ "arn:aws:s3:::com.mybucket.betterez.bucket" ] }, { "Effect": "Allow", "Action": [ "s3:PutObject", "s3:GetObject", "s3:DeleteObject" ], "Resource": [ "arn:aws:s3:::com.mybucket.betterez.bucket/*" ] } ]}
- Give the new policy a name that you can remember, e.g. betterez bucket access policy. You should also use the description.
- Go back to the IAM console, and select the user you’ve created.
- Click add permissions and then Attach existing policies directly. You should see your newly created policy. Click review and add permissions.
Your new bucket is now ready to use with the user you’ve created!